Application Security - Triple A framework
What is security?
Application-level security measures that prevent data or code in an application from being stolen or hijacked. It includes security considerations that occur during application design and development, but also concerns systems and approaches to protecting applications after they are deployed.
- A process and tools for securing software.
- Application security is the process of making apps more secure by finding, fixing, and enhancing the security of apps.
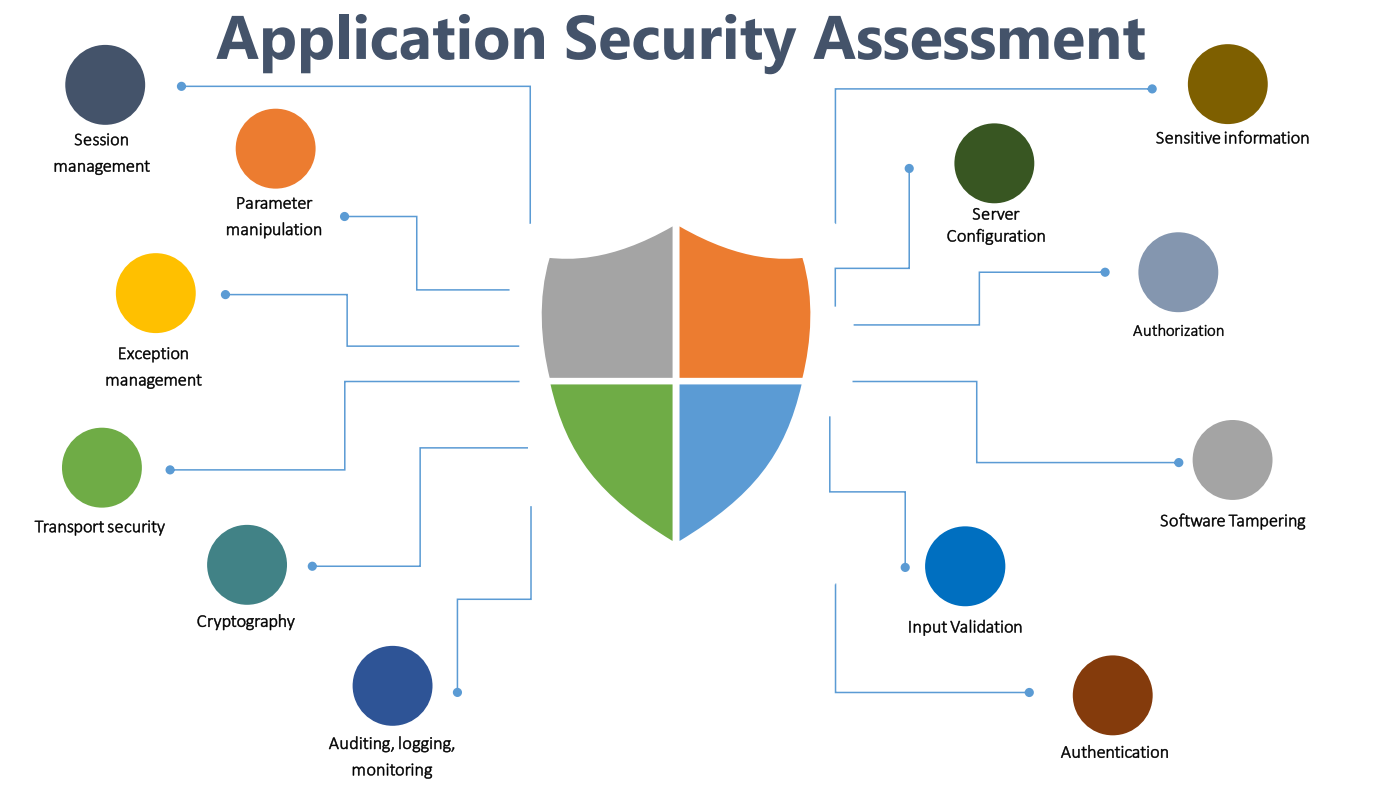
- Session management: Session hijacking; session replay; man in the middle
- Parameter manipulation: Query string manipulation; form field manipulation; cookie manipulation; HTTP header manipulation
- Exception management: Information disclosure; denial of service
- Transport security: gain access to encrypted blocks of data (authentication and confidentiality) during transport using SSL
- Cryptography: Poor key generation or key management; weak or custom encryption
- Auditing, logging, monitoring: User denies performing an operation; attacker exploits an application without trace; attacker covers his or her tracks
- Sensitive information: Access sensitive code or data in storage; network eavesdropping; code/data tampering
- Configuration management: Unauthorized access to administration interfaces; unauthorized access to configuration stores; retrieval of clear text configuration data; lack of individual accountability; over-privileged process and service accounts
- Authorization: Elevation of privilege; disclosure of confidential data; data tampering; luring attacks
- Software Tampering: Attacker modifies an existing application’s runtime behavior to perform unauthorized actions; exploited via binary patching, code substitution, or code extension
- Input Validation: Buffer overflow; cross-site scripting; SQL injection; canonicalization
- Authentication: Network eavesdropping; Brute force attack; dictionary attacks; cookie replay; credential theft
3 Triple A Framework
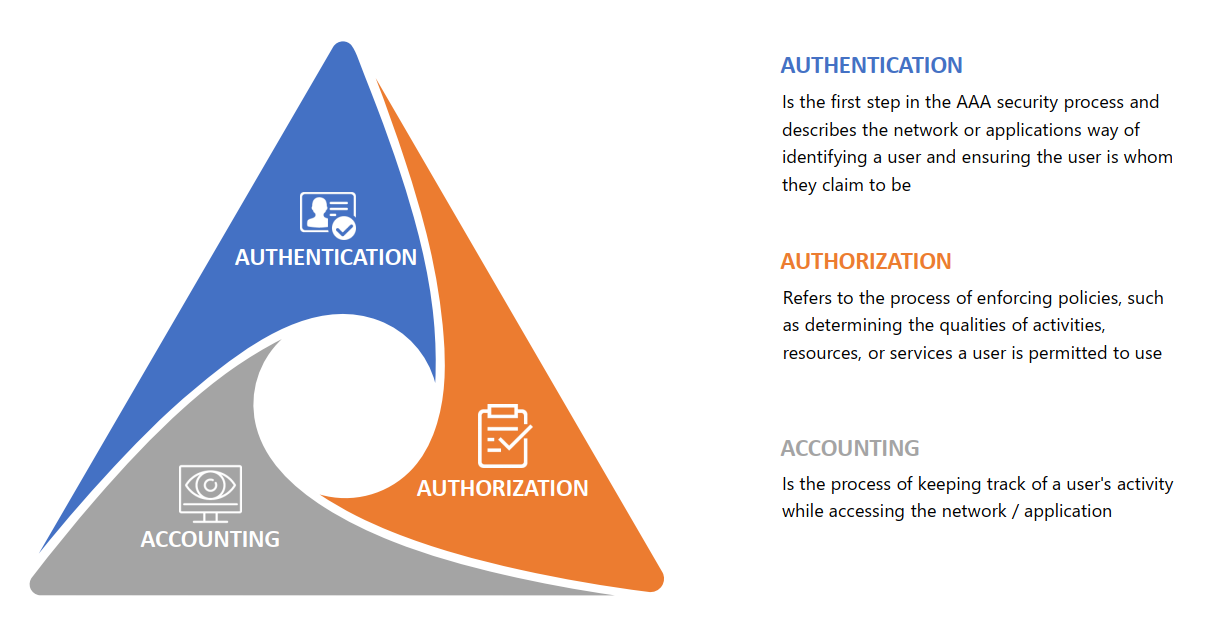
- Authentication, authorization and accounting (AAA) refers to a common application security framework for mediating network and application access. AAA intelligently controls access to computer resources by enforcing strict access and auditing policies. This process ensures that access to network and software application resources can be restricted to specific, legitimate users.
- The AAA Framework is a simple way to understand security issues surrounding the access ability of individuals within an organization. The Internet Engineering Task Force researched and coined the acronym in the early 2000s. The 3 As stand for Authenticate, Authorize and Account. Understanding and crafting policies around this framework can help make systems more secure.
Using the AAA Framework and drilling down into the components helps people understand the basic nuances of identity security.
Authentication: Who you are?
- Authentication is the first step in the AAA security process and describes the network or applications way of identifying a user and ensuring the user is whom they claim to be. The user enters a valid username and password before they are granted access; each user must have a unique set of identification information. Identification can be established via passwords, single sign-on (SSO) systems, biometrics, digital certificates, and public key infrastructure.
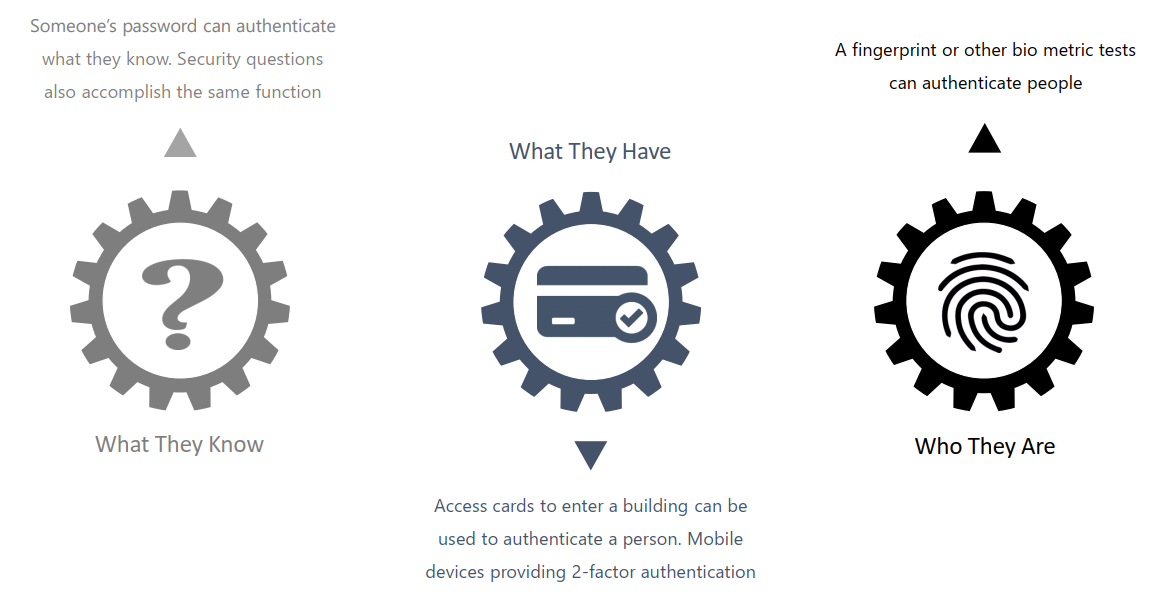
- Authenticating users is the first step in a secure identification system. The system needs to make sure the person accessing a system is who they say they are. The method of authenticating a person can fall into three main categories:
- What They Know: Someone’s password can authenticate what they know. Security questions also accomplish the same function.
- Who They Are: A fingerprint or other bio metric tests can authenticate people.
- What They Have: Access cards to enter a building can be used to authenticate a person. Mobile devices providing 2-factor authentication also use what a person has to verify identity.
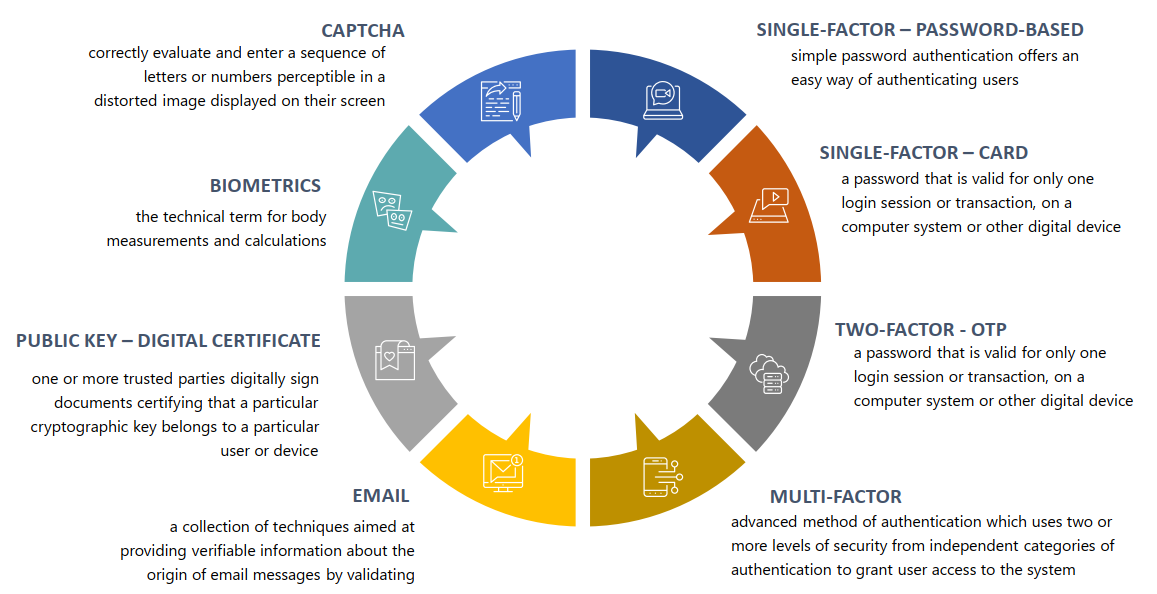
- Single-Factor Authentication – It’s the simplest authentication method which commonly relies on a simple password to grant user access to a particular system such as a website or a network. The person can request access to the system using only one of the credentials to verify his identity. The most common example of a single-factor authentication would be login credentials which only require a password against a username.
- Two-Factor Authentication – As the name suggests, it’s a two-step verification process which not only Two a username and password, but also something only the user knows, to ensure an additional level of security, such as an ATM pin, which only the user knows. Using a username and password along with an additional piece of confidential information makes it virtually impossible for fraudsters to steal valuable data.
- Multi-Factor Authentication – It’s the most advanced method of authentication which uses two or more levels of security from independent categories of authentication to grant user access to the system. All the factors should be independent of each other to eliminate any vulnerability in the system. Financial organizations, banks, and law enforcement agencies use multiple-factor authentication to safeguard their data and applications from potential threats.
- Captcha test.
- Biometric authentication.
- Email Authentication
Authorization: What you can do?
- Authorization refers to the process of enforcing policies, such as determining the qualities of activities, resources, or services a user is permitted to use. Authorization usually occurs within the context of authentication; once you have been authenticated, AAA security authorization assembles the set of attributes that describe what you are authorized to perform.
Users are assigned authorization levels that define their access to a network and associated resources. For example, a user might be able to type commands, but only be permitted to show execute certain commands. This may be based on geographical location restrictions, date or time-of-day restrictions, frequency of logins, or multiple logins by a single user. Other types of authorization include route assignments, IP address filtering, bandwidth traffic management, and encryption. An administrator may have privileged access, but even they may be restricted from certain actions.
For example, in more secure application architectures passwords are stored salted with no process for decrypting. These secure applications enable passwords to be changed (with existing passwords being overridden), but never retrieved.
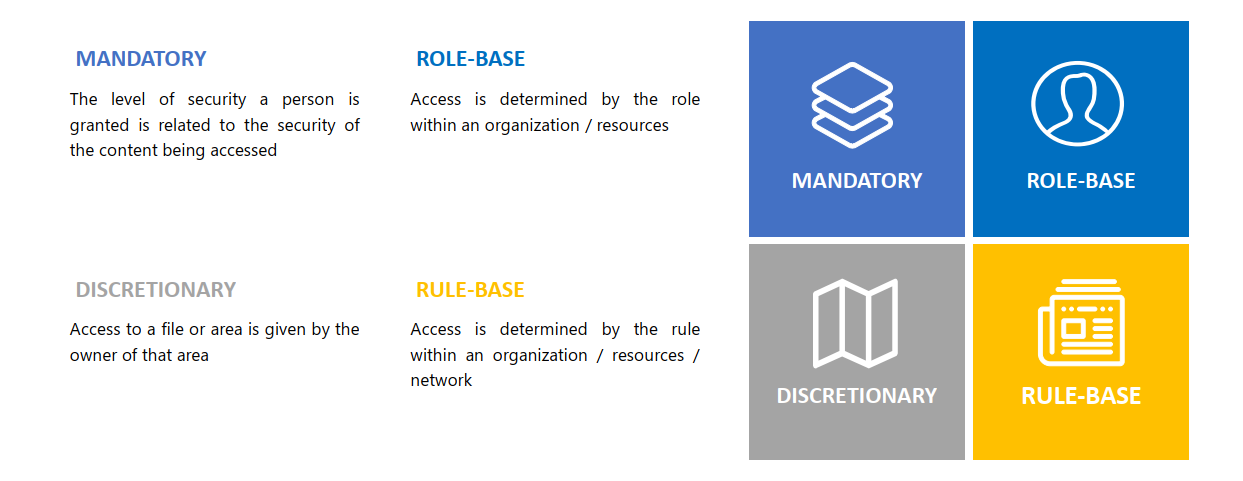
AAA security authorization allows you to enforce this restriction.- Mandatory Access Control (MAC) – The level of security a person is granted is related to the security of the content being accessed. This is common in military use-cases.
- Discretionary Access Control (DAC) – Access to a file or area is given by the owner of that area. An example of this framework is a Google doc where access can shared by the creator with whoever they desire.
- Role-Based Access Control (RBAC) – Access is determined by the role within an organization. For example, the shipping department might have access to inventory but not marketing collateral.
- Rule Based Access Control (RBAC) - Access is determined by the rule. For example, A rule might be to allow access to an IP address but block that IP address from use of a specific port, for example port 21 commonly used for FTP, or port 23 commonly used for Telnet.
- OAuth (Open Authorization)
Accounting
- After a person begins logging into a network and working, their usage should be monitored
- Is the process of keeping track of a user’s activity while accessing the network involves collecting statistics and usage information for a particular user or class of users
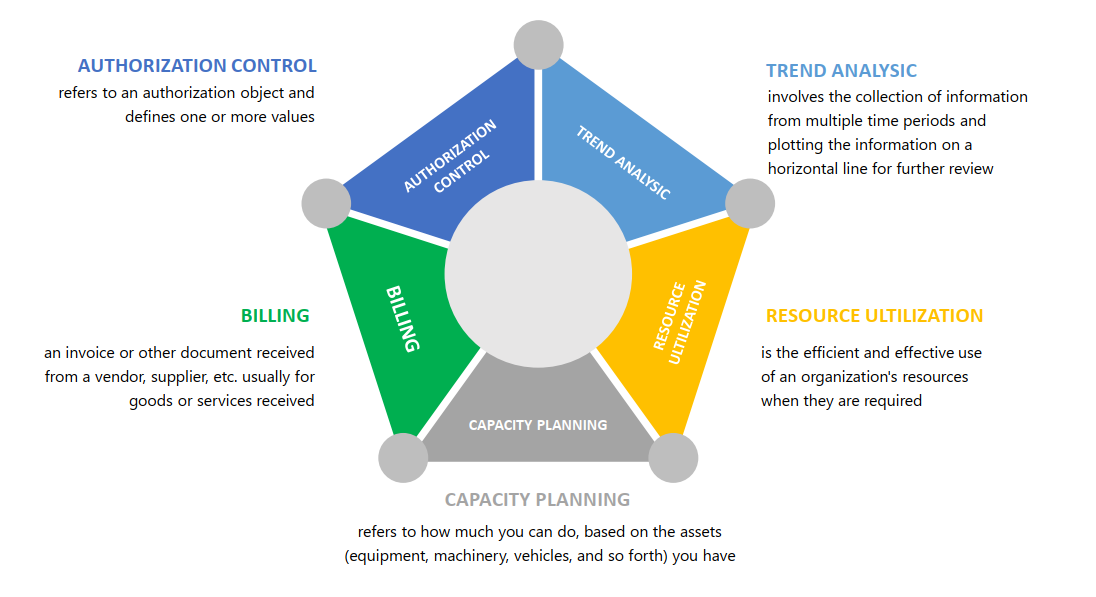
- Used for authorization control, billing, trend analysis, resource utilization, and capacity planning activities.
References:
- Wikipedia